IGEL Blog

Accelerating Comply-to-Connect and Zero Trust with Cisco ISE and IGEL UMS
Why Zero Trust Needs More Than “Designed In”
Mission-critical organizations such as the Department of War (DoW) face growing pressure to enforce Comply-to-Connect (C2C) and Zero Trust Network Access (ZTNA) requirements. These frameworks demand proof that every device is trusted, compliant, and properly configured before it touches the network – a Zero Trust Secure Enclave.
A Zero Trust Secure Enclave is a specialized, highly secure computing environment designed to enforce Zero Trust principles—which assume that no user, device, or system should be trusted by default, even if it’s inside the network perimeter.
Here’s a breakdown of the concept:
Zero Trust Principles
- Never trust, always verify: Every access request is authenticated, authorized, and encrypted.
- Least privilege access: Users and systems get only the minimum access necessary.
- Continuous monitoring: Behavior is constantly monitored for anomalies.
- Micro-segmentation: Network and system resources are divided into isolated zones to limit lateral movement.
By combining Cisco Identity Services Engine (ISE) with the IGEL Universal Management Suite (UMS), organizations can quickly establish a Zero Trust Secure Enclave—one where:
- Only endpoints enrolled in UMS can connect.
- ISE interrogates UMS for compliance validation
- Future capability will include policy enforcement dynamically, adapting to the endpoint’s confidence level and trust state.
This approach reduces complexity, ensures C2C compliance, and lowers cost by leveraging IGEL’s secure OS and centralized management.
IGEL’s Preventative Security Model™
In previous blogs, we discussed how organizations can rethink their endpoint strategy using IGEL with the foundation being the IGEL Preventative Security Model™. IGEL provides the secure, immutable endpoint platform required for Zero Trust:
- Read-Only OS: Linux-based, tamper-proof, and hardened, reducing attack surfaces.
- No Local Data Storage: Prevents sensitive data leakage.
- Curated App Portal: Only IGEL validated applications can run.
- FIPS 140-3 Level 1 Encryption (in progress): Meets stringent DoW security standards.
- Extended Hardware Lifecycles: Repurpose existing PCs and laptops with IGEL OS for compliance without expensive refreshes.
- IGEL Managed Hypervisor extending capabilities to guest OS, legacy apps, and managing virtualization at the edge for IT and OT
- Zero Trust Secure Enclave supports compliance with emerging Zero Trust requirements for OT
Active UMS and Cisco ISE: Enabling the Secure Enclave
The IGEL Universal Management Suite (UMS) is at the core of this Secure Enclave. The integration of UMS and Cisco ISE provides:
- Centralized Enforcement: Only UMS-enrolled devices are validated and granted access.
- Single Source of Truth: ISE queries UMS via REST APIs to check enrollment, firmware, and compliance attributes.
- Dynamic Policy Enforcement: ISE applies segmentation, VLANs, or quarantines based on trust.
Integration with Cisco ISE
- Enrollment: Devices must be UMS-enrolled to request network access.
- Validation: ISE queries UMS to verify enrollment and compliance.
- Access Decision: Based on posture and trust level, ISE enforces access rules (least privilege, segmentation, or denial).
- Remote Attestation: Confirms device posture and configuration.
- Continuous Monitoring: ISE revalidates endpoint configurations against UMS, ensuring ongoing compliance.
- Policy Push (Next Step): ISE will be able to dynamically push policies back to UMS to enforce endpoint configurations by trust level and persona, not just hardware.
Real-World Mission Assurance
IGEL + Cisco ISE integration delivers:
- Automated C2C posture checks.
- Zero Trust enforcement across users, devices, networks, and applications.
- Policy-driven workload segregation for internal and external users.
- Lower cost and complexity through repurposed hardware and simplified endpoint management.
- Ability to support OT and IT devices/environments for zero trust and policy enforcement
Industries including defense, finance, healthcare, and critical infrastructure are adopting this architecture for ZTNA convergence, supporting not just compliance but operational resilience.
Architecture in Practice
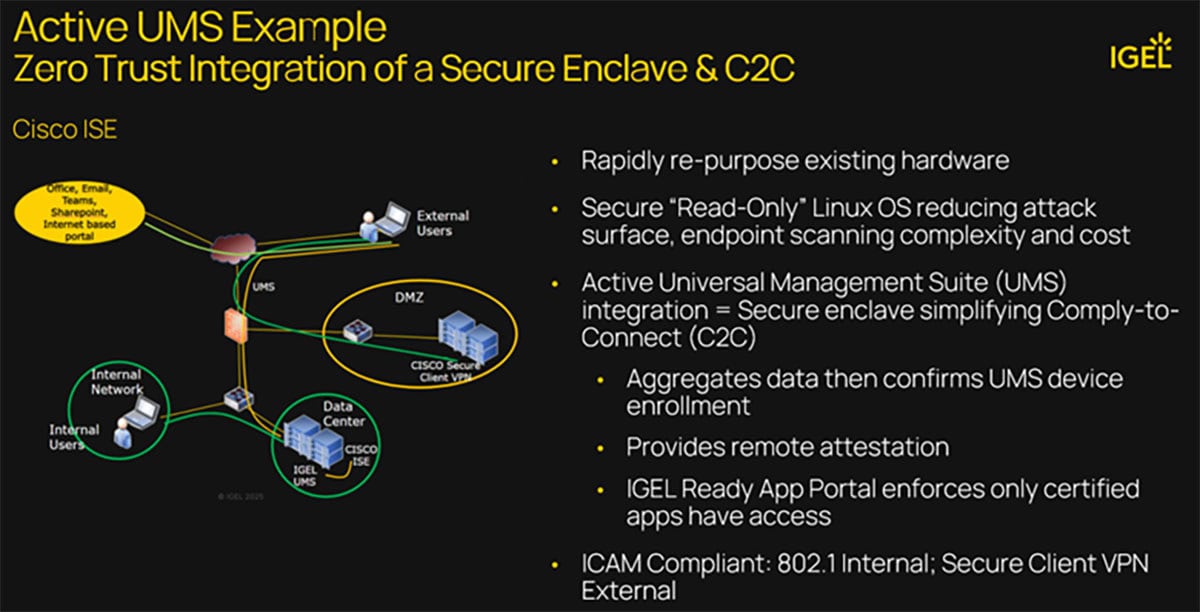
This architecture demonstrates how:
- UMS confirms device enrollment.
- ISE aggregates data and applies access decisions.
- IGEL OS ensures endpoints are immutable, attested, and running only certified apps.
- Continuous monitoring + enforcement maintain compliance over time.
With Cisco ISE + IGEL UMS, organizations can confidently implement Zero Trust Secure Enclaves that meet Comply-to-Connect requirements, simplify enforcement, and reduce cost.
Learn how IGEL can accelerate your Zero Trust and Comply-to-Connect initiatives. Contact us at [email protected].


